Exchange Online / Microsoft Azure is under constant development by Microsoft. Features may move to other portals, disappear or new features may be added. This guide reflects the status as of 2025.
Whitelisting of IP-Adress and Domain via "Advanced Delivery Role"
1. Open Microsoft Security Center
2. In the Security Center go to Policies & Rules, to Threat Policies and there, under Rules to the Advanced Delivery rule. There, click on the Phishing Simulation tab.
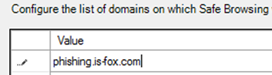
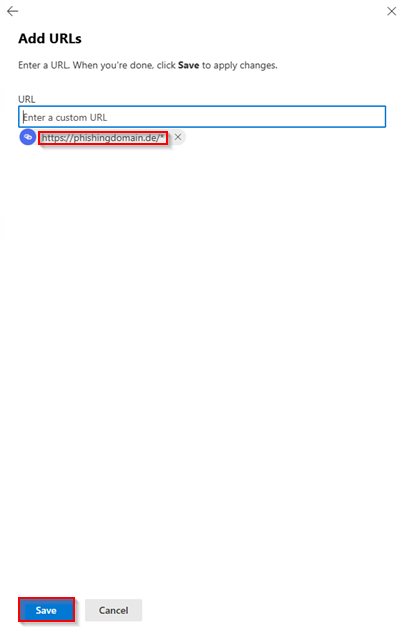
3. Use Add to enter the sending domain of the e-mail under Sending Domain, and the IP address of your phishing server that is sending the e-mail under Sending IP.
So, if you want to send a phishing simulation from the sender alert@microsoft-security.com, the domain to be entered is microsoft-security.com.
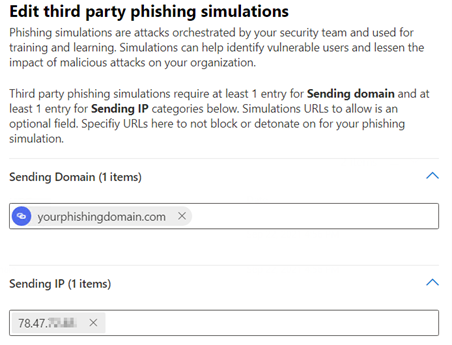
According to Microsoft documentation, these settings virtually disable all security checks unless the email contains real malware.
- Filters in Exchange Online Protection (EOP) and Microsoft Defender for Office 365 don't take actions.
- Zero-hour Auto Purge for SPAM and Phishing (ZAP, emails detected as malicious can be automatically removed from users' mailboxes) doesn't take actions.
- Automated investigation and response (AIR) in Microsoft Defender doesn't take actions.
- Safe Links in Defender for Office 365 does not block the identified URLs and attachments.
- System Alerts are not triggered.
- If the email is reported via the Microsoft Report Phishing button, admins receive a message in the Azure Security Portal under Submissions that the message is part of a phishing simulation and not a real threat.
For more information about security settings in Exchange Online, seehttps://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/configure-advanced-delivery?view=o365-worldwide
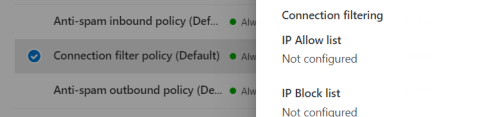
Whitelisting of IP address in "Anti-spam policy"
1. Open Microsoft Security Center.
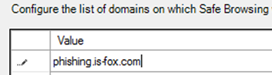
2. Go in the Security Center to Policies & Rules, to Threat Policies and there under policies to Anti-spam policy. There you add the IP address of your phishing server in the Connection filter policy.
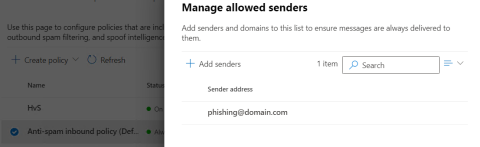
3. Stay with the anti-spam policies and switch to the anti-spam inbound policy. There add the sender address of the phishing simulation.
Creating a Mail Flow Rule in the Exchange Online Admin Center
Attention: the Exchange Online Admin Center probably needs different credentials than the Microsoft Security Center:
1. Open Exchange Online Admin Center and go to rules.
2. Add a new rule using the plus symbol.
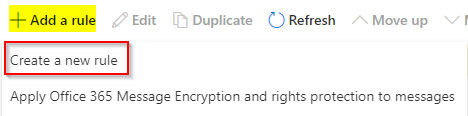
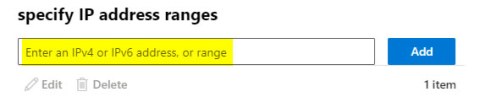
3. Enter the IP address of your phishing server.
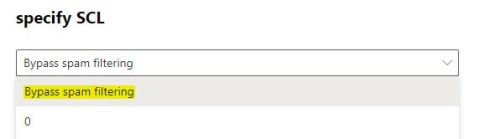
4. Select the "Bypass spam filtering" option under "specify URL"
5. Name the new rule e.g. "Bypass phishing mail" and select the fields to be filled in according to the screenshot below.
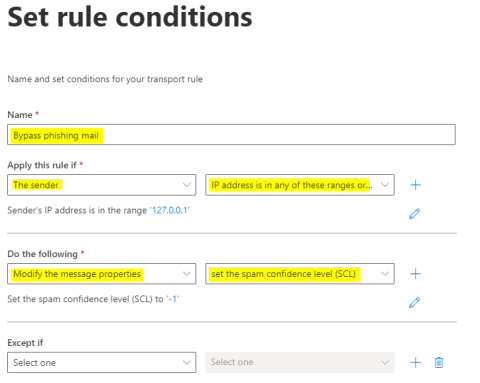
With these settings, you have now activated the "ultimate switch off". Please remember to reverse the settings after the phishing simulation.